Well this is a year old vulnerability but I thought of documenting it as was quite famous.
and was over television news. Here are some links
http://indiatoday.intoday.in/story/Chinese+hackers+target+PMO/1/79215.html
http://www.wired.com/threatlevel/2010/01/operation-aurora/.
Enough of stories.
Lets move on to technical analysis.
I picked up a POC from internet and tested on my XP SP2.
I opened IE in windbg and opened the POC html with IE. IE crashed at following location.
Looking at the disassembly of the location:
We see the the Crash happens at the GetDocPtr
It looks like the address pointed by ecx register has invalid data which causes the access violation.
Looking at the stack trace
Looking at the function mshtml!CEventObj::GenericGetElement
It looks like ecx value is derived from the value at address pointed by esi.
restart windbg and set breapoint
bp mshtml!CEventObj::GenericGetElement+0x97
the press g. when internet explorer comes up open the html page.
We break at the point and view the contents of address pointed by esi.
0:000> dds poi(esi) l1036f7b30 7d4c1850 mshtml!CImgElement::`vftable'0:000> dds ecx l1036f7b30 7d4c1850 mshtml!CImgElement::`vftable'
We see that the that the ecx points CImgElement Vtable is
Looking at the Vtable
0:000> dds 7d4c1850 l107d4c1850 7d6de377 mshtml!CImgElement::PrivateQueryInterface7d4c1854 7d4f43c9 mshtml!CElement::PrivateAddRef7d4c1858 7d4f4cdd mshtml!CElement::PrivateRelease7d4c185c 7d519a0e mshtml!C1DElement::`vector deleting destructor'7d4c1860 7d56c685 mshtml!CImgElement::Init7d4c1864 7d56c5e0 mshtml!CImgElement::Passivate7d4c1868 7d63ba1f mshtml!CBase::GetEnabled7d4c186c 7d63ba1f mshtml!CBase::GetEnabled7d4c1870 7d63b1f2 mshtml!CBase::GetPages7d4c1874 7d63b644 mshtml!CBase::InterfaceSupportsErrorInfo7d4c1878 7d6df0f8 mshtml!CImgElement::QueryStatus7d4c187c 7d6dff5f mshtml!CImgElement::Exec7d4c1880 7d4fad5c mshtml!CRect::CRect7d4c1884 7d4f4e9d mshtml!CElement::SecurityContext7d4c1888 7d4f7c1c mshtml!CBase::SecurityContextAllowsAccess7d4c188c 7d5e71d8 mshtml!CElement::DesignMode
We can use the following winbg command to automate to see what all variables are created at esi at the address
bp mshtml!CEventObj::GenericGetElement+0x93 ".printf \"esi = [%08x] \",esi;dds poi(esi) l1;gc"I press g in windbg and see the following
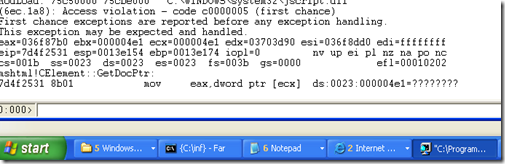
esi = [036f7f20] 036f7b30 7d4c1850 mshtml!CImgElement::`vftable'esi = [036f7f20] 036f7b30 7d4c1850 mshtml!CImgElement::`vftable'ModLoad: 75c50000 75cbe000 C:\WINDOWS\system32\jscript.dllesi = [036f6b60] aaaaaaaa ????????(8b8.768): Access violation - code c0000005 (first chance)First chance exceptions are reported before any exception handling.This exception may be expected and handled.eax=036f7bc0 ebx=aaaaaaaa ecx=aaaaaaaa edx=03703cd0 esi=036f6b60 edi=ffffffffeip=7d4f2531 esp=0013e154 ebp=0013e174 iopl=0 nv up ei pl nz na pe nccs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00010206mshtml!CElement::GetDocPtr:7d4f2531 8b01 mov eax,dword ptr [ecx] ds:0023:aaaaaaaa=????????
We see that esi always points the CImgElement is created at the place.
Restart windbg clear all the old breakpoints using bc *.
Let us find which all function cause the exception and
I set another breapoint
bp mshtml!CEventObj::GenericGetElement+0x97
and run windbg. Windbg breaks at the following location
Breakpoint 0 hiteax=0013e4c8 ebx=036f7b30 ecx=036f7b30 edx=0013dfc0 esi=036f7f20 edi=ffffffffeip=7d6d5250 esp=0013df7c ebp=0013df98 iopl=0 nv up ei pl nz na po nccs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00000202mshtml!CEventObj::GenericGetElement+0x97:7d6d5250 e8dcd2e1ff call mshtml!CElement::GetDocPtr (7d4f2531)
Lets set breakpoint at the address pointed by ecx and see which function write on the address ecx=036f7b30
After the breakpoint is hit I clear all the breakpoints and set breakpoint on write
ecx=036f7b30
0:000> bc *0:000> ba w4 036f7b30 ".printf \"eip=[%08x] \n\n \",eip;u eip l1;gc"0:000> geip=[7d519a43] mshtml!CElement::~CElement+0x10:7d519a43 7406 je mshtml!CElement::~CElement+0x18 (7d519a4b)ModLoad: 75c50000 75cbe000 C:\WINDOWS\system32\jscript.dlleip=[7d4f2c22] mshtml!CStr::Set+0x3e:7d4f2c22 83c004 add eax,4(464.960): Access violation - code c0000005 (first chance)First chance exceptions are reported before any exception handling.This exception may be expected and handled.eax=036f8a50 ebx=aaaaaaaa ecx=aaaaaaaa edx=03703df0 esi=036f7fc0 edi=ffffffffeip=7d4f2531 esp=0013e154 ebp=0013e174 iopl=0 nv up ei pl nz na pe nccs=001b ss=0023 ds=0023 es=0023 fs=003b gs=0000 efl=00010206mshtml!CElement::GetDocPtr:7d4f2531 8b01 mov eax,dword ptr [ecx] ds:0023:aaaaaaaa=????????
It looks like some of the functions which write the address are
shtml!CElement::~CElement
mshtml!CStr::Set




No comments:
Post a Comment