I have been using the Far Manager and Hiew Combo for a really long time while doing Malware Analysis . (Unfortunately I could not fix the formatting issues to words the end of the blog)





Searching Files in a Directory:
This is done by pressing alt+(alphabets of the key- u can use wildchars too).
Sorting files in a directory:
Creating shortcuts to directories and accessing them:
Far Manager is not a malware Analysis tool at all but an alternative to windows explorer . But certainly it solves some basic level of problems for malware analysis like sorting based on size, see hidden files ,view processes . Far manager is a command line alternative to windows Explorer(Explorer.exe) which is used to browse the file system .It speeds up your work as it is you can browser your file system quicker the the conventional windows explorer . you can do a lot of quick stuff using keyboard shortcuts . Don't worry about remembering shortcuts. After sometime it will be on your finger tips.
You can download far manager from https://farmanager.com/. You can run it by extracting and double clicking the Far.exe .Default far manager has two panes left and right. you can two locations of you file system at a time.left side pane is displaying contents in folder "C:\Program Files\7-Zip" and right side pane is displaying contents in folder "D:\books\c-prog" . you can browse through files in the directories using up and down arrow keys. cursor is the green color.
At the bottom you can see 1.Help, 2.User Menu,3.View..... 5.Copy
This means F5 is used for copy. If you want to explore more options press the keys left ctrl+ right ctrl, left shift, right shift , alt and see whether these options change.
If I press ctrl, I see 12-sort . Now if I press ctrl+F12 let's see what happens .
You can sort the files in the directory using size,extension etc. Note:This can be useful for analysts when they are dealing with huge set of files. Often malwares in a same family which are close to each other have similar size. You can sort by size and cluster the same size files.
The cursor or control is on left pane on the file "History.txt" . If you want to copy paste History.txt from "C:\Program Files\7-Zip" to "D:\books\c-prog" you need to press F5. For cut paste you need to press F6. See how quick it is to do a cut paste. Multiple files can be copy pasted at same time. to select a file to copy paste you need to press "shift+down/up arrow" key. Same keys for de-selecting a selected file. To select all the files below the cursor you need to "shift+right arrow" for above "shift+left arrow". you can then use F5 or F6 for starting the copy .
to shift between the panes or go from "C:\Program Files\7-Zip" to "D:\books\c-prog" , you can press tab. You can use use up and down arrow keys to browse the files in same directory.
The exe is green(7z.exe,unistall.exe) colored text and directory is white("lang").
If you want to open a file in directory you just need to move the corsor there and then press enter. An exe will execute and a .txt file will open in notepad. Hidden files are seen in light blue color. This can be often used in malware analysis if the malware hides any of it's dropped file by using hidden properties of windows .
You can see more details of files in the directory by pressing “”left Ctrl + 3”. you can see the extension, file size, creation date time
We can also browse directories using keyboard shortcuts .If you want to go into the "lang" directory move your cursor to lang using the up or down arrow key and then press enter. If you want to go to the directory above press "Ctrl + pgUp".
Searching Files in a Directory:
This is done by pressing alt+(alphabets of the key- u can use wildchars too).
you can sort files in a directories by pressing F12. This gives you option to sort by size,extension,write time etc .you can use this feature to cluster similar size files etc
Creating shortcuts to directories and accessing them:
save shortcuts to directories- you can save upto 10 directories in shortcut with keys 0 to 9.
To create shortcut for directory go to the directory on number 1 and press :ctrl+shift+1 .
Now to go to the shortcut saved in number 1 key press right ctrl +1 . similarly you can create shortcuts to 10 directories .
Adding tool Shortcuts to Far Manager:
As malware researcher we need to use all lot of tools on the samples. you can add shortcuts of tools to far manager. I want to add hiew (hacker's view) to my far manager and would like to open samples with it.
To add a command I need to press F2.


Adding tool Shortcuts to Far Manager:
As malware researcher we need to use all lot of tools on the samples. you can add shortcuts of tools to far manager. I want to add hiew (hacker's view) to my far manager and would like to open samples with it.
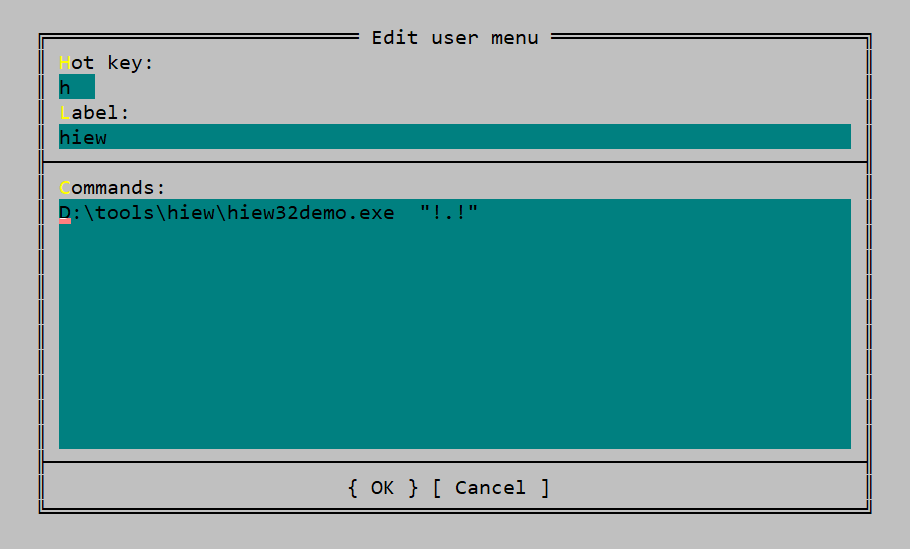
Before adding hiew to Far, I have downloaded hiew from http://www.hiew.ru/ and extracted to "D:\tools\hiew" in my system. I need to Hiew32Demo.exe to the Far manager.
to open a file in hiew ,from command line, I need to type the command hiew32demo.exe file__full_path where file__full_path is the parameter to hiew32demo.exe .
you can see a window popping up over far manager which asks you to press Del,Ins,F4, Alt+F4 keys . you can try out each of these keys. To add Hiew I press Ins key.
Label is just for your reference ,I have added hiew here. I commands I have put D:\tools\hiew\hiew32demo.exe "!.!" . Here "!.!" means selected file which is the parameter to hiew32demo.exe .
Now hiew is added to my tools. In order to open a file in hiew I can browse to a files then press F2+h to open the file in Hiew.
Hiew to be continued in next blog.